Purpose of this document
This document provides information to assist Customers and Partners who want to use Cursum to store content containing personal data. Specifically, it describes how Customers and Partners can use Cursum’s services in compliance with the European Parliament and the council regulation (EU) 2016/679 of 27 April 2016 on the protection of individuals with regard to the processing of personal data and on the free movement of such data. This whitepaper also contains documentation on how Cursum complies with the regulation and which measures that have been implemented to ensure proper handling of personal data.
Terminology
- Data controller – can either be a customer or a partner. A data controller decides the purpose and manner for the processing of the data.
- Data processor – Cursum is the data processor and processes data on behalf of a data controller.
- DPO or Data Protection Officer – data protection officers are responsible for overseeing the data protection strategy and implementation to ensure compliance with GDPR requirements.
- Cursum Learning Center or CLC – The LMS (Learning Management System) owned by Cursum A/S.
- Cursum – Owner of CLC
- User – a person that is registered as a user in CLC and that has been marked as Active in CLC.
General overview
About Cursum Learning Center
About Cursum Learning Center CLC (Cursum Learning Center) is an online learning and communication management system. CLC is built on a Microsoft .NET-based platform and can be integrated with existing systems to enable organizations to build, administer, and report on courses, exams and questionnaires to users using the Internet. It also contains extensive dashboard functionality with statistical reports on user progress. Employees and students can automatically take courses when needed and can repeat lessons and quizzes for maximum learning retention.
Responsibility
The responsibility can be divided into three areas as illustrated below. This highlights the main responsibilities for each party involved. Responsibility overview:
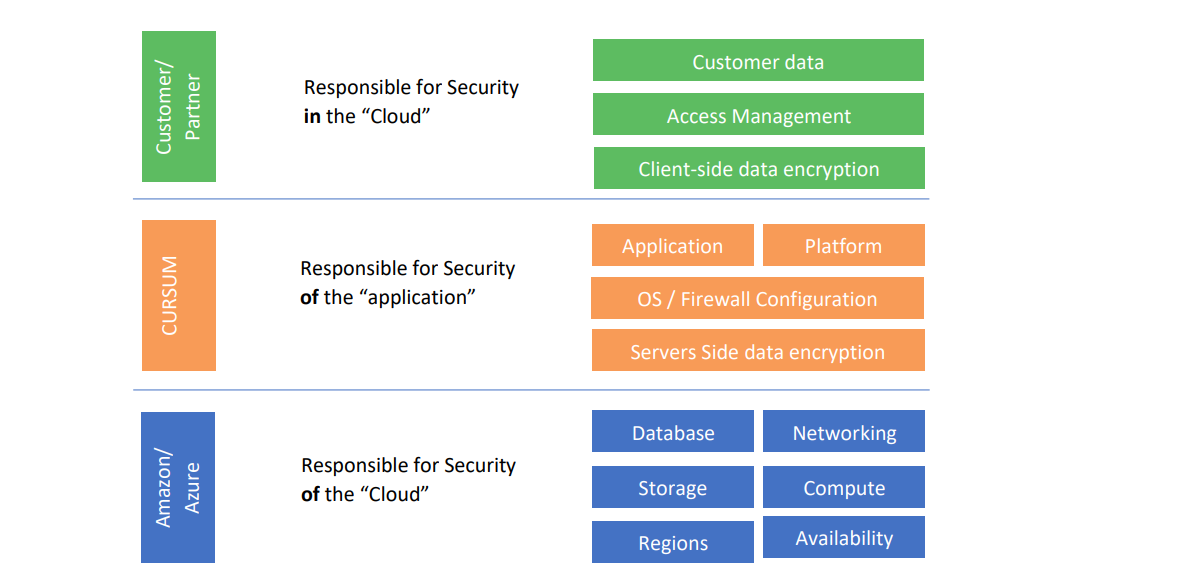
Azure operates, manages and controls the components from the host operating system and virtualization layer down to the physical security of the facilities in which Azure operate. Cursum is responsible for the application and platform hosted on the infrastructure provided by Azure Cursum is responsible for the management of the guest operating system (including updates and security patches to the guest operating system) and associated application software, as well as the configuration of the security firewall and other security-related features.
The customer will generally connect to the application and environment through services provided by third parties (for example, internet service providers). Cursum or Azure does not provide these connections, and the customer should consider the security of such connections and the security responsibilities of such third parties in relation to their systems.
This is really no different from working Storage Compute Database Networking Regions Availability Azure Responsible for Security of the “Cloud” CURSUM Responsible for Security of the “application” Customer/ Partner Responsible for Security in the “Cloud” Application Platform Customer data Access Management OS / Firewall Configuration Servers Side data encryption Client-side data encryption with a network service provider who brings connectivity to on-premises data centers. The customer is also responsible for all customer data entered into the system and extracted from the system including personal data, text, and video content. Cursum has no influence on and is not monitoring this content.
Basic diagram of the application
LC is a .net cloud-based application based on C# with IIS/WebApp and Microsoft SQL Server as its database engine.
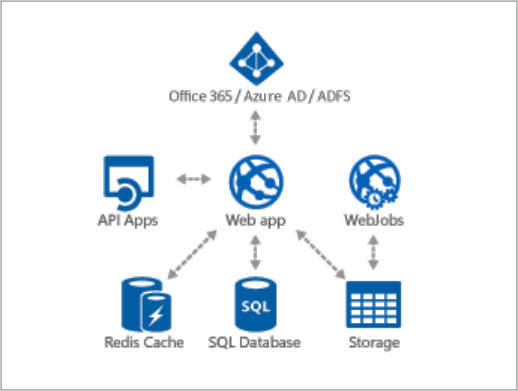
LC is a standard asp.net 4.5 web application with Microsoft SQL server database as its backend datastore. Depending on the server setup, it can run the scheduled recurring jobs as a background service using a classic Windows service, using hangfire on single IIS installations or web jobs on Azure.
Depending on the customer size and license agreement, each client has its own SQL database with its data securely separated from other clients.
The system design related to access and content is defined by a Multitenancy SaaS based on a “Standalone single-tenant app with single-tenant database” design. This ensures the above-mentioned segregation of data.
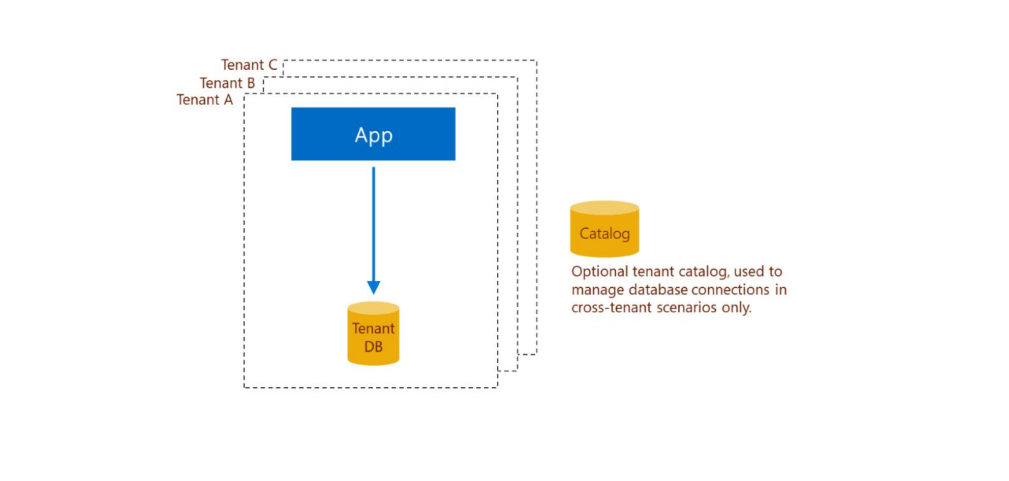
Storage and database
Depending on the installation and customer needs, LC supports Microsoft SQL 2008 and upwards plus Azure SQL. Any files uploaded or generated by the system are stored under the IIS file system or in the database.
Azure Blob Storage File Access Design
The system architecture intentionally uses Azure Blob Storage as the content repository for the platform. This design choice is not a security flaw or a breach. It is a standard, secure, and purpose-built approach that enables the platform to deliver the following functionality:
- Embedding files directly in HTML pages (e.g., course content, certificates, and learning materials)
- Integrations with external services such as video streaming, document rendering, and analytics
- High performance and fast global delivery of static content
- Alignment with common web architecture practices for modern SaaS systems
Files stored in Azure Blob Storage are not publicly discoverable. They cannot be indexed by search engines or browsed. A file can only be accessed if the requester knows the full, system-generated URL. This form of access is intentional and required for correct system operation.
Because this setup is fundamental to platform performance and functionality, it is not something that should be modified or restricted beyond the existing access controls already in place.
Security
The security is based on the guidelines that Microsoft use, we refer to their documentation on compliance which is available here:
https://azure.microsoft.com/nb-no/support/legal/subscription-agreement/
Collection of personal information
Cursum provides an online platform (LC) for completing course activity available to the customer/data controller. The platform basically contains no personal data. The Customer is solely responsible for the data created and loaded in LC and the customer can create and load data without Cursum having knowledge, consent, or notification of any kind.
Data flow
The purpose of this section is to document and highlight the main data flows related to personal data. In short, this relates to:
- What format the data transfer takes, for example, by email, phone, fax or paper
- Whether the connection is secure, encrypted, masked and so on
- Who or what "touches" the data
- Whether the data is stored securely
Data Flow overview
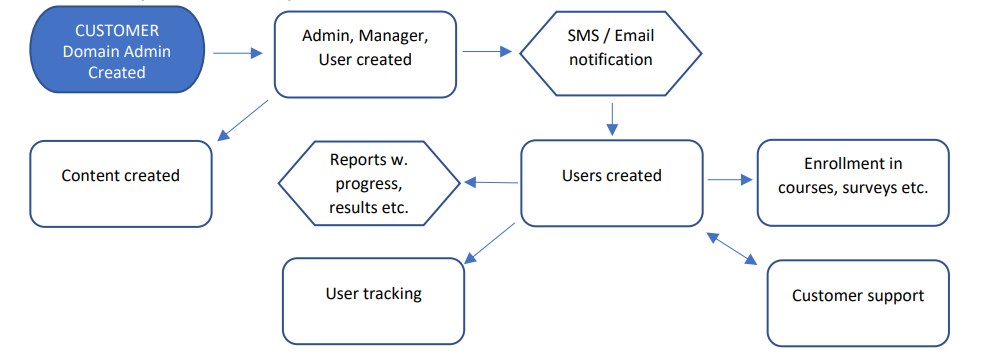
The following diagram gives a high-level overview of the data flow in the LC.
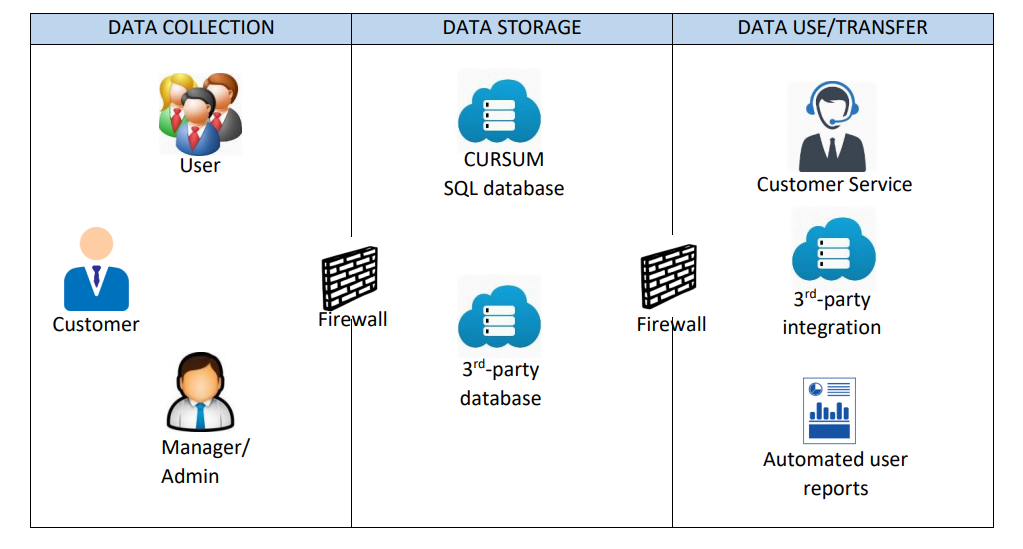
In short, the customer domain is created by Cursum or its partners and customers. This is the foundation of the activities in the LMS. The customer or partner decides who should have access to the application.
Admins, managers and users are created and enrolled, obligations based on the access given should be communicated, documented and in some instances formally signed. Cursum ensures that data is securely created and stored in a SQL database behind firewalls. If a third-party database is integrated, for example, for user creation and maintenance, the security is obliged to be ensured by the customer or partner.
Data is used by the users, managers, admins and to some extent the Customer Service department. It is possible to extract data or automate reports. Use, storage and maintenance of these reports is the customer or partner’s responsibility and should be handled with care and in respect of the confidentiality of data. If third-party integration is used, Cursum maintains the APIs used for integration and data is transferred securely based on agreed credentials.
Data flow (detailed view)
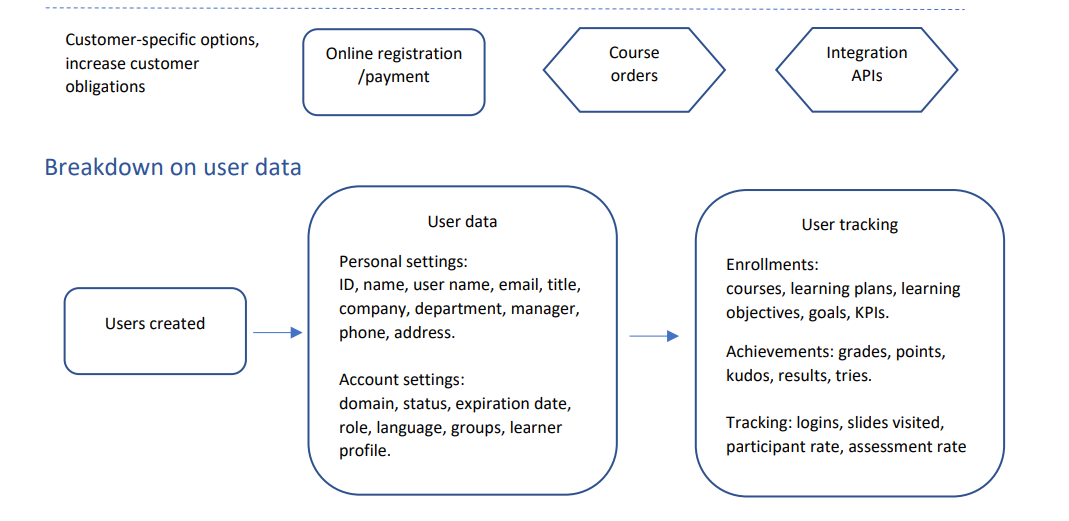
The user data and user tracking is stored in the database in a secure environment by our provider Azure. Upon request, the data and tracking will be deleted from the LC, the process is described in the following sections. There will be no traceable data stored on the user, they will be deleted from the database, in future reports and tracking.
Risk assessment
Cursum has assessed the risk management procedures based on the following steps. These steps cover the risk picture for Cursum LC:
A. Scope Definition
B. Identifying and Analyzing risks
C. Managing and Monitoring risks
Scope definition
The risk assessment purpose is to define clear roles, processes, and responsibility to evaluate current and future risks and to ensure that the risk level is minimized and monitored. Cursum has the following internal roles that support the Customer and the internal procedures in Cursum as an organization. All employees at Cursum have signed a confidentiality agreement that highlights the importance of data protection and upholding the compliance of data security.
| Roles |
Tasks |
System Role |
|
Developer/Designer
|
Building new functionality in the LC
|
|
|
Tester/Release Manager
|
Ensuring quality control, use cases, compliance
|
DPO maintaining compliance
|
|
Sales/Presales/Account Manager
|
Ensuring customer dialogue of current and new customers
|
|
|
Support
|
Maintaining customer and partner dialogue
|
Data supporter
|
|
Management CTO / CEO
|
Daily management of business, leadership, contract and legal obligations.
|
CTO - System Owner
|
To ensure increased focus on the data protection, Cursum has appointed a Data Protection Officer (Release Manager). This person’s primary function is to monitor the organization for compliance to the regulation and ensuring the appropriate protection of the information that the organization holds. The rules and regulations around appointment of a DPO have been properly defined and is part of the monitoring.
Support cases
In a support case, customers requesting personalized data are only processed if the requester is identified and validated as a receiver of the information. This can require a consent from our contact person at the partner or customer.
Risk identification
The purpose of this section to identify the risks to LC. Risks occur in IT systems when vulnerabilities (flaws or weaknesses) in the IT system or its environment can be exploited by threats (from natural, human, or environmental factors). The risk level will be categorized in three levels to increase transparency and focus on the most essential risks possible.
| Risk Level |
Risk Description & Necessary Actions |
|
High
|
The loss of confidentiality, integrity, or availability could be expected to have a severe or catastrophic adverse effect on organizational operations, organizational assets, or individuals.
|
|
Moderate
|
The loss of confidentiality, integrity, or availability could be expected to have a serious adverse effect on organizational operations, organizational assets, or individuals.
|
|
Low
|
The loss of confidentiality, integrity, or availability could be expected to have a limited adverse effect on organizational operations, organizational assets, or individuals.
|
The specific risk elements are divided into four main categories which comply to the risk overview:
| Category |
Category Description |
|
Process (P)
|
Process that involves creation, usage, and procedures regarding updates, personnel and behavior related to the system.
|
|
Access (A)
|
Access meaning both physical and virtual access to either hardware or software, covering also access to integrated platforms
|
|
Hardware & third-party software (HS)
|
Physical hardware and third-party software related to databases and connected software
|
|
External (E)
|
External dimension related to disasters, environmental, or functional happenings.
|
Based on these categories the risks are described and controls are defined to ensure proper handling of data.
| Risk cat. |
Vulnerability |
Threats |
Risk of Compromise of |
Risk Summary |
Risk Level |
|
P
A
|
1. Patches to correct flaws in application
|
Computer crime
Malicious use System compromise
Unauthorized access
|
Confidentiality and integrity of data
|
Exploitation of flaws in application software could result in compromise of confidentiality and integrity of data.
|
Low
|
|
2. Loss of firewall protection
|
Firewall failure can result in increasing the likelihood of other risks being exploited.
|
Low
|
|
3. Key person dependency
|
Loss of a key person could result in system downtime if a software issue occurs or the inability to enhance or maintain this system’s functionality
|
Medium
|
|
4. Inadequate customer practices
|
Data corruption or loss, or implementation of applications with errors could result from improper or incomplete testing of the system or application changes.
|
Low
|
|
5. Poor systems and password practices
|
Unsafe handling of passwords can lead to malicious use and jeopardization of the integrity of data.
|
Low
|
|
1. Remote access to server console not properly monitored.
2. Internal access to the server.
3. Single point of failure
4. Loss of critical documentation, data or software
5. Integration to external systems
|
System compromise
Unauthorized access
Malicious use
System unavailable
|
Confidentiality and integrity of corporate data
|
Remote access control. If these controls are not in place, unauthorized access could result in compromise of the confidentiality and integrity of data.
Remote access control. If these controls are not in place, unauthorized access could result in a compromise of the confidentiality and integrity of data.
Loss of any portion of the system could result in the entire system or some portion of the system being unavailable.
Loss of documentation, software or data could result in data compromise and temporary disruption in service, or inability to restore services which have been lost.
|
Medium
Medium
Low
Low
|
| Risk cat. |
Vulnerability |
Threats |
Risk of Compromise of |
Risk Summary |
Risk Level |
|
HS
|
1. Hardware issues/equipment failure or loss
2. Inadequate database support
3. Inadequate software support
|
System unavailable
Computer crime, malicious use, system compromise, unauthorized access
|
Inability to access the system.
Confidentiality and integrity of corporate data.
|
Loss of hardware or equipment would result in the entire system or some portion of the system being unavailable.
Software and database issues caused by the vendor could lead to data corruption or mission-critical system disruption or dysfunction.
|
Low
Low
|
|
E
|
1. Natural disaster
2. Environmental issues
3. Functional lockout
|
Hurricanes, floods, and other weather phenomena. Loss of AC or power.
|
Inability to access the system.
|
Natural disasters could interrupt power to the computer center and make it impossible for staff to support the server environment thus disabling access.
Environmental issues could result in the inability to access and maintain server hardware.
The inability of staff to access the computing infrastructure or applications could result in the inability to access the system.
|
Low
Low
Low
|
Managing and Monitoring Risks
In this section, we identify the relevant measures to ensure that controls are defined to cover risk scenarios described in section Risk Identification.
| Risk category |
Relevant controls |
|
Process
|
- Cursum has a well described process for introducing new software patches both on local installations and in terms of its own cloud solution.
- Test methods before patch release are described.
- Alarms that monitor eventual malicious system behavior have been defined. These alarms inform key personal for quick response.
- Cursum has documented classification of the sensitivity of the Cursum LC. The purpose is to monitor most sensitive areas. Quarterly revisions are conducted.
- Passwords for both local installations, Cursum.net and major admin accounts are stored safely and changed every three months. On each hosting installation, there is an identifier that informs the CTO if any abnormal activity has been registered.
|
|
Access
|
- Required IT security roles have been assigned in writing, the DPO has been assigned and monthly meetings regarding security have been established where controls are conducted.
- External access to customers servers is defined and coordinated with each individual customer, and the guidelines from the customer are followed.
- The number of Major Admin accounts has been reduced to a minimum and only assigned to key personnel. Customers are advised to follow the same safety regulations.
- Backup of data is being conducted as a standard procedure. Data is backed up daily between 3am and 5am. The backup set consists of both backup of the website and the database (data and transaction logs). All backups are stored within the same datacenter region. So, for example, if the customer is running on an Azure instance on the West Europe data center, all data both production and backups are kept within that region.
|
|
Hardware and 3rd Party Software
|
- LC hardware and database is either hosted by Azure or
- locally at the customer, Cursum provides SaaS and has no access to the specific hardware. The providers have a very high standard for ensuring security and uptime.
- Updates of servers, firewalls and related security measures are continuously implemented and monitored.
- Updates of servers, firewalls and related security measures are continuously implemented and monitored.
|
|
External
|
There is no additional process implemented that is not covered in the previous sections.
|
Data retention, deletion, and breach
Personal data should not be kept (in an identifiable form) for longer than is necessary for the purposes for which the personal data was collected or further processed.
Customers
It is the customer who decides what the personal data stored in the application can be used for and for how long it is necessary to retain that personal data. The customer can delete or anonymize the personal data when it is no longer needed.
Cursum has no insight into whether stored data includes personal data or to what purposes the customer is processing any particular data which it has stored in the cloud. Accordingly, Cursum cannot determine for how long it is necessary to retain the data in order to achieve that purpose.
When a customer deletes its content from the Cursum services, the content is rendered unreadable or disabled and the underlying storage areas on the Azure network used to store the content are wiped, prior to being reclaimed and overwritten, in accordance with Azure standard policies and deletion timelines. Azure procedures also include a secure decommissioning process conducted prior to disposal of storage media used in accordance with industry-standard practices.
Data Breaches
Customers retain the responsibility to monitor their own environment for privacy breaches and to notify regulators and affected individuals as required under applicable law. Only the customer is able to manage this responsibility. Customers control their own access keys and determine who is authorized to access their Cursum account.
Cursum does not have visibility of access keys, or who is and who is not authorized to log into an account; therefore, the customer is responsible for monitoring use, misuse, distribution, or loss of access keys. Where required by applicable law, Cursum will promptly notify the customer if Cursum has actual knowledge of a confirmed breach of the Cursum security standards relating to the platform.
Timelines and details have been established requiring customers to notify the authorities within 72 hours and the specific individuals without undue delay. Notifications must include the nature, identity, recommended measures to prevent adverse effects, and how the organization will address the breach. Cursum’s process in case of a breach is shown in this diagram:
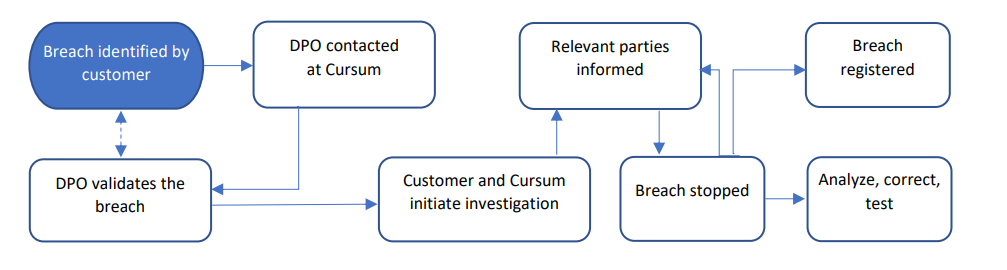
The breach must be analyzed, corrected, and tested before LC is online and used for course activities again.
Handling of Security Breaches and Information Security Incidents
Notification Routines for Security Breaches
- We continuously monitor systems to identify potential threats and security incidents.
- Upon detecting a security breach, we immediately assess the criticality of the incident and classify it as low, medium, high, or critical.
- If the incident is deemed high or critical, the customer will be notified within 24 hours of detection.
- Regular updates on the incident and corrective actions are provided.
Handling of Information Security Incidents
- When a security incident occurs, we follow a structured approach to manage the situation effectively.
- All information shared with the customer and users is handled through secure channels to ensure confidentiality and integrity in communication.
- All incident handling complies with GDPR and other relevant regulations.
Improvement of Routines
- After an incident, we conduct an in-depth root cause analysis to identify the underlying causes.
- We regularly review and update our security policies to ensure continuous improvement based on new threats and technologies.
- Employees are regularly trained in security protocols, ensuring they are prepared to handle future incidents effectively.
Structured Approach to Managing Security Breaches
- Immediate Detection and Assessment
- Upon detecting a potential breach, our team quickly assesses the situation to determine the scope and criticality. We classify the incident as low, medium, high, or critical based on its impact on data confidentiality, integrity, and availability.
- Containment and Mitigation
- Immediate steps are taken to contain the breach, limiting its spread or impact. This could include isolating affected systems, stopping unauthorized access, or applying security patches.
- Communication and Notification
- We promptly notify affected parties, including the customer, within 24 hours if the breach is high or critical. We provide regular updates on the status of the situation and corrective actions being taken.
- Analysis and Correction
- After containment, we analyze the cause of the breach and work to correct the vulnerabilities or flaws that led to it. This includes technical remediation and reviewing policies or processes that may need improvement.
- Post-Incident Review and Learning
- Once the breach is resolved, we conduct a thorough review to document lessons learned and take preventive measures to avoid future incidents. This may involve updating our security protocols or providing additional training to employees.